
Starting September 1, 2025, Texas Senate Bill 2610 gives small Texas businesses legal protection from punitive damages after a data breach.

Firms that invest in structured Bentley onboarding programs set themselves apart by improving consistency, accelerating productivity, and reducing costly errors from day one.
Struggling with ProjectWise? From tangled permissions to storage bloat and file lock chaos, here's how to fix the admin nightmares slowing your team down.
.png)
Think your team has OpenRoads Designer figured out? These five signs might prove otherwise—and show you where major time and value are being lost.
Relying on informal training for Bentley Systems leads to costly inefficiencies, inconsistent project delivery, and lost profit—especially for engineers and project managers in civil firms.

Power BI helps AEC firms turn disconnected project data into real-time insights, enabling faster decisions, better resource management, and stronger profitability.
Egnyte offers a flexible alternative to ProjectWise, supporting both design and non-design teams across platforms.

OpenRoads Designer and how its thoughtful application, paired with proper training, can unlock significant value for engineering teams.

With rising demands for ORD experts, engineering firms are turning to Fractional CADD Managers as a cost-effective alternative to FTEs.

Power BI helps AEC firms turn disconnected project data into real-time insights, enabling faster decisions, better resource management, and stronger profitability.
With Windows 10 ending in October 2025, now’s the time to validate hardware, test software, and plan your Windows 11 rollout to avoid costly disruption.
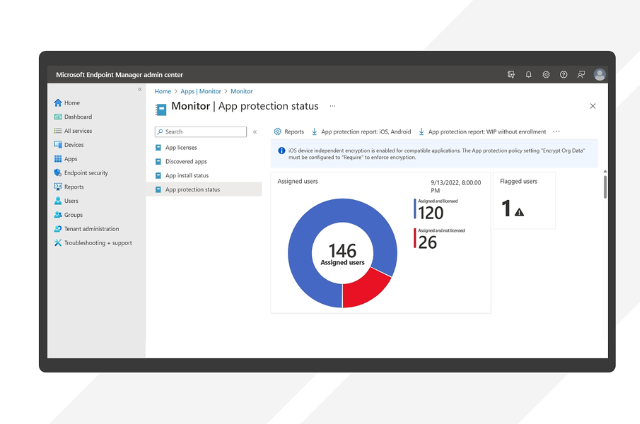
Thinking about ditching Group Policy or SCCM? Here’s how moving to Intune can finally make device management less chaotic—and a lot more cloud-smart.

Cloud-based PC management lets your team securely configure, update, and support devices anywhere—reducing IT headaches and accelerating onboarding.

Starting September 1, 2025, Texas Senate Bill 2610 gives small Texas businesses legal protection from punitive damages after a data breach.
.png)
As threats become more advanced, adopting a Zero Trust security model—where no user or system is trusted by default—has become essential to limit risk, control access, and protect critical data.

IAM is critical for AEC firms to protect sensitive data, control user access, and maintain compliance across increasingly complex digital environments.

Strong data governance is essential for protecting sensitive information, minimizing security risks, and ensuring regulatory compliance.